Because it is difficult to design and construct a secure system, developers failed to take the necessary precautions. However, they fall short of ensuring security by protecting it against vulnerabilities in advance.
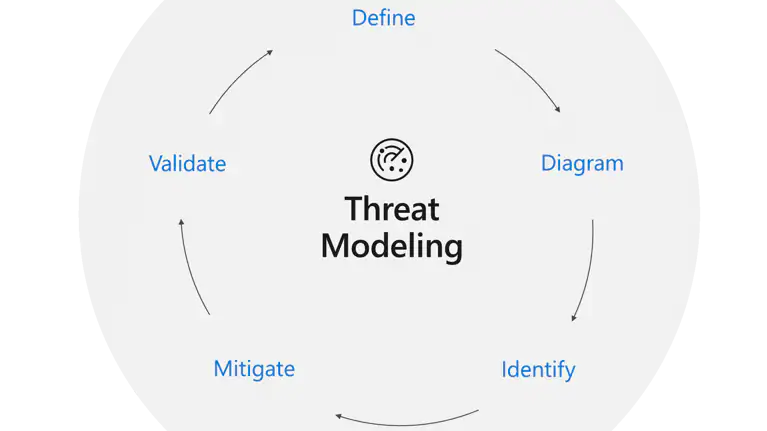
In this method, establishing a Threat Modeling with STRIDE can resolve the reaction to anticipate such a circumstance in the future. Threat modeling excludes coding reviews and security testing. This decently organized process and favorable arrangement ensure that the application developers could develop security systems.
Need for designing such systems
Systems are frequently designed to accommodate business demands. Threat modeling, however, is an approach that aids businesses in identifying security threats and application vulnerabilities at the design stage. It is necessary because resolving security concerns found during testing is time-consuming and costly.
Now let’s use an example to better understand the Threat Modeling approach before businesses adopt it. An analyst learns during the entry testing phase that a programmer/aggressor could manipulate the request while creating a solicitation, assuming that “Threat Modeling” hasn’t been applied on the current site. He can alter the shipment address and order price.
Reasons for the vulnerability of the site
The following are a few reasons for the vulnerability of the website to such risks:
- Customers were allowed to carry out fundamental transactions without reconfirming.
- Before managing the input data, permission was not completed
- Blunder responses revealed sensitive data, such as system information, session identification, or record data.

How businesses may exploit threat modeling to mitigate similar risks in the future?
Every organization approaches threat modeling differently as draughtsmen depending on the requirements of a project. The five steps for securing a company’s system using risk display have been listed below.
- Identify security targets
Understand security requirements and potential risks in business processes to reach your goals.
- List available resources and environmental factors
The security architect has to be aware of a list of resources for protecting themselves from prospective attackers.
- Identify the regions you can trust
The entry-exit emphasis for each trust area must be understood by developers.
- Identify the possible risks and weaknesses
Consider risks that would primarily impact the company’s system rather than doing a broad lookout for threats following a predetermined path like STRIDE.
- Identify the content threat model
Threat modeling is a common practice, and documentation has become vital responsibility of the organization’s team. Designers and developers may build secure designs and eliminate any security issues related to a design by using documentation.
